Vulnerability testing

Do we do vulnerability testing?
The short answer is yes, but the real question is, is that enough? After all, you, as a developer, create software with the help of our tool and add your code, so eventually, the absolute safety of the application is a combination of both. PHsPeed has a lot of protection built in. There are several tokens, like CSRF, and there is protection against XSS and SQL injection. We try to keep up with the libraries we use to avoid introducing vulnerabilities.
Automated vulnerability tools of commercial parties can scan your website. Some parties can scan your code, and you pay per line of code. That makes it quite expensive, and it never replaces the work of a real ethical hacker. But there are ways that you can use to verify the created project for vulnerabilities, and I like to show you the results of ZAP, an open source and free tool from the OWASP community. This tool is able to scan your project and I will explain the result of one of our applications here.
This is the customer portal that you find on our website. In the next screenshot you see the result of a ZAP scan:
If you want to do something similar then download ZAP from the OWASP website, and use localhost:8010/your application to scan. So what does the scan tell us?
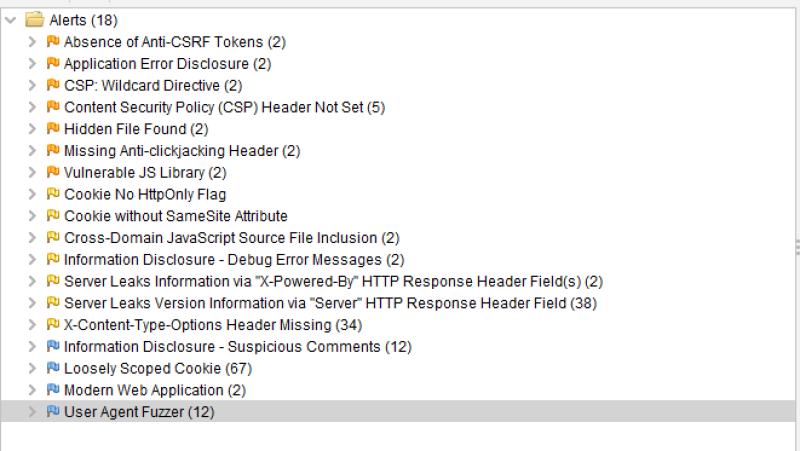
There are 18 notifications. So let's look into them one by one:
- The first message complains about the absence of a CSRF token.
This is a false positive message as PHsPeed does use a CSRF token, but ZAP does not recognize it. You can easily verify this by not touching your application for 10 minutes and then trying to continue. You will get a csrf error message. You will find the code in your main application: NoCSRF::check('main_csrf', $_POST, true, 60*10, false ); // 10 minutes one-time mode - Application error disclosure
This notification tells us that we display errors when they occur in the code. That is a severe issue when the application is in production. You do not want error messages to appear when the application crashes for any reason. PHsPeed requires you to promote your code so that all debugging info is removed from your production code. But while developing, you want the messages because you need to be able to debug. So this warning is of no meaning here, but is, when you have this in your production environment. - CSP wildcard directive
Content Security Policy (CSP) is an added security layer that helps detect and mitigate certain types of attacks. Including (but not limited to) Cross-Site Scripting (XSS), and data injection attacks. These attacks are used for everything from data theft to site defacement or distribution of malware. CSP provides a set of standard HTTP headers that allow website owners to declare approved sources of content that browsers should be allowed to load on that page — covered types are JavaScript, CSS, HTML frames, fonts, images, and embeddable objects such as Java applets, ActiveX, audio and video files. This must be configured on the web server, which is not the case in our development environment. But PHsPeed does generate code to force this in the html meta code. - Content Security Policy (CSP) Header Not Set (5)
This is similar to the message above. - Hidden File Found (2)
We have a Xampp environment set up for development, NOT production. The two hidden functions are server-info and server-status, used for debugging. But in your production environment, this should be configured out, as you never should give information about your environment to (potential) hackers. - Missing Anti-clickjacking Header (2)
This message applies to a missing setting in relation to IFrames. PHsPeed does not use IFrames. - Missing Anti-clickjacking Header (2)
This is a message that you should take very seriously, and it refers to outdated libraries. We have upgraded the libraries already, but this is a good showcase of an issue you might find. If you open the item, you will see which library(s) needs updating. - Cookie No HttpOnly Flag
This flag is forced in the generated PHP code (when you have configured that in the project options), but it depends on your installation if this setting applies or not. For development, this is not an issue, but in production, you need to see what your provider can do (as it can be set in php.ini, on the web server, or with the provided code below if the function is enabled).
if(session_set_cookie_params([
'path' => '/',
'domain' => 'localhost',
'httponly' => true,
'samesite' => 'Strict',
'lifetime' => 3600
])==false ){
die('failed to set cookie parameters');
} - Cookie without SameSite Attribute
See above. - Cross-Domain JavaScript Source File Inclusion (2)
This message refers to a javascript library imported from an external website. In this case, Google. PHsPeed uses internal libraries by default (which is advised by OWASP) and avoids importing them, although you can choose to do so in the preferences. But some libraries cannot be stored locally. - Information Disclosure - Debug Error Messages (2)
This is the same as described under 'Application error disclosure.' - Server Leaks Information via "X-Powered-By" HTTP Response Header Field(s) (2)
It should be disabled on the web server level. For our development environment, this is not an issue. - Server Leaks Version Information via "Server" HTTP Response Header Field (38)
It should be disabled on the web server level. For our development environment, this is not an issue. - X-Content-Type-Options Header Missing (34)
For mimed information, you can set a sniffing parameter. It is a low-risk item and not commonly used (yet) - Information Disclosure - Suspicious Comments (12)
This report gives information about static texts in your (javascript) code. It does on every string like: module&&module.exports?module.exports=b(require("jquery")):" where it triggers on 'jquery'. Although it is good to verify all the reported items, it is usually not an issue. - Loosely Scoped Cookie (67)
Cookies can be scoped by domain or path. This check is only concerned with domain scope. The domain scope applied to a cookie determines which domains can access it. For example, a cookie can be scoped strictly to a subdomain, e.g., www.nottrusted.com, or loosely scoped to a parent domain, e.g., nottrusted.com. In the latter case, any subdomain of nottrusted.com can access the cookie. Loosely scoped cookies are standard in mega-applications like google.com and live.com. Cookies set from a subdomain like app.foo.bar are transmitted only to that domain by the browser. However, cookies scoped to a parent-level domain may be transmitted to the parent or any subdomain of the parent. - Modern Web Application (2)
This is an informational alert, so no changes are required. No links have been found while there are scripts, which is an indication that this is a modern web application.
Good to know that we have created something that is considered to be modern ;-) - User Agent Fuzzer (12)
Check for differences in response based on fuzzed User Agent (e.g. mobile sites, access as a Search Engine Crawler). Compares the response status code and the hashcode of the response body with the original response. Actually not an alert either.
Conclusion. The application we tested has no High-risk items, a few medium risks (due to the fact that the web server used is configured for development and testing and a library with a newer version), and a few low-risk items. Considering the result, updating the libraries fixes all issues here.
The main question is now, is the application safe? Well, to a certain extent. No application is 100% safe, and this is an automated test. It is helpful, but an actual penetration test by an ethical hacker is always advised, especially if you manage critical data. But it is obvious that we do our checks often and are continuously aware of threats. But in the end, you, as a user, are creating applications. Therefore you have your own responsibility to verify the quality of the result. No 2 applications will be the same; therefore, ALWAYS do your own testing! If you have vulnerabilities that you believe are the result of some mishap in our code, report these, and we will do our utmost best to fix them with #1 priority.
Happy coding!